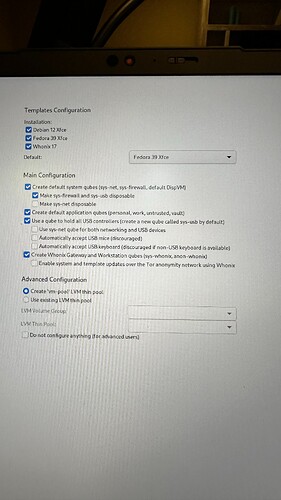
I was curious if there are specific configurations that one should be selecting after installing QubesOS and on the “template configuration” screen? Stick with the defaults or is it good to enable any other flags?
The defaults are very good. I’ll offer some of my commentary for others in the future:
-
Debian, Fedora, Whonix - unless if your disk space is limited, get all three. Whonix is needed for anonymity and Tor, Fedora is decent OOB security (hence why dom0 is Fedora), and many devs only package software for Debian (because Ubuntu is Debian-based).
-
System qubes - you want these. They are annoying to configure yourself, and generally unhelpful if you did. Firewall and USB disposable is good and will probably never be a hindrance. Disposable Net qube is good to use, but keep in mind that it will wipe your WiFi authentication history after reboot. That’s too inconvenient for me, so I leave it off.
-
App qubes - really helpful to have them when you are new to Qubes. Once you are comfortable with the architecture and have decided on specific workflows, I think you would uncheck this and build what you want. For example, I do all of my “personal,” “work,” and “untrusted” activites in disposable qubes, with the exception of specific ones like an “email” qube or a “development” qube that are normal AppVMs.
-
USB qube - arguably essential. I am surprised they still give the option at install. Combining Net and USB into one qube can be convenient; however, consider the security implications of hooking potential USB malware to a Network connection. I would not recommend it, unless if you have a specific need. Even so, I would build something separate and reach out to the devs for help.
-
Mice and Keyboard - After much testing, I see no need to enable the Mice. Just leave it off. The Keyboard, on the other hand, is essential for a desktop install and convenient for laptop if you frequent use your laptop at your desk with a separate keyboard. I do, so I check that one. But this leaves you susceptible to Bad USB. So consider your threat model.
-
Whonix - I recommend these, though I then delete anon-whonix after install. I think all Torified work should be ephemeral, with the exception of hosting a Monero wallet over Tor. But, when you are new to Qubes, just like with the other AppVM default qubes, I recommend keeping anon-whonix.
-
Updates over Tor - really slow and inconvenient. Not recommended on a daily driving laptop unless if you need it (again, threat model considerations).
-
Advanced - only if you have a strong understanding of LVM pools. I do not, and am unsure how you could benefit anyway.
Hope this helps someone!